Abstract
Imagine making a credit card payment with just a selfie or having a virtually unhackable password without memorizing a single character. With the advancement of biometric security measures such as facial recognition, consumers will no longer have to imagine a world where this is possible. The technology that has been in development since the late 1960s is now readily available for everyday use. Facial recognition technology has applications in a number of industries. One particular industry that looks to implement the new technology is security. Banks, airports, and even smartphone manufacturers are now looking to incorporate facial recognition into their basic security infrastructure.
Introduction
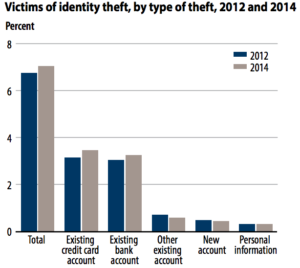 Figure 1: Since 2012, the frequency of identity theft has risen, thus leading individuals to look for more effective methods to protect themselves from theft [10].
Figure 1: Since 2012, the frequency of identity theft has risen, thus leading individuals to look for more effective methods to protect themselves from theft [10].
The push for facial recognition technology is emerging in tandem with a rising concern amongst the general population regarding the safety of their online identities. During 2014, approximately 17.6 million Americans had their identity stolen. Of those 17.6 million, 86% reported unauthorized activity on existing bank accounts and credit cards [10]. Using biometrics for security purposes has become increasingly attractive because of new developments that improve accuracy and reliability. In particular, facial recognition is used to secure smartphones, authenticate money transfers, and search for suspects hiding in large crowds.
Facial Recognition vs. Other Methods of Security
Moving away from typed passwords and other biometric security options such as fingerprint scanning appeals to many because of how easily an identity thief can guess a person’s password or create a replica of their fingerprint.
[2]. The complexity of measurements needed to identify an individual’s face makes facial recognition more secure. Additionally, recent improvements to the technology have increased the accuracy of facial recognition to well over 90%, putting it on par with other biometric security measures [1].
Facial recognition also prevails over other methods of security in its ability to gather biometric data in crowd settings. With facial recognition, law enforcement can strategically place cameras around a designated area rather than funneling everyone through a stall that reads their fingerprint. This not only eases the flow of traffic in places such as airports or arenas but also serves as a discreet way of searching for a suspect without alerting them to any extra security presence [3].
How Does Facial Recognition Work?
In order for facial recognition to be effective, the algorithm used must be able to distinguish between different facial features, handle aging, poor lighting, varying orientations of a person’s head in different images, and a variety of emotions. This is easier said than done since any movement by an individual will alter the composition of a photograph, even if pictures are taken consecutively [8]. However, all of these requirements can be accomplished in the two main steps of the facial recognition process: detection and identification.
Face Detection
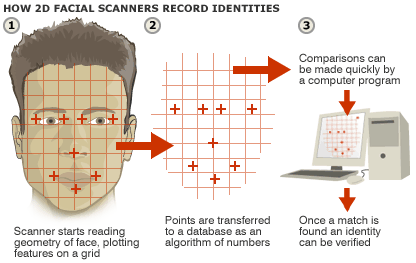
The first step is face detection, where an algorithm determines the boundaries of an individual’s face. The algorithm accomplishes this task by sorting through all the pixels in an image in order to determine which pixels make up the face it is attempting to analyze. This process is important because without providing constraints for the algorithm to operate, distances between nodal points will become skewed. Nodal points are measurable endpoints on an individual’s face that can be used by the code to determine the distances that facial features are away from each other (see Figure 2) [7]. If the distance between nodal points becomes too large the program will pass the image off as an inanimate object rather than a human face.
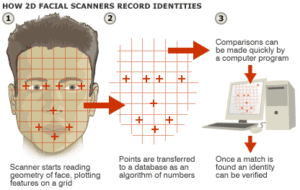
Figure 1: This diagram goes over the basics of the face recognition process [1].
Pixel Separation
The separation of pixels to detect the boundaries of a face is most commonly done through the Viola-Jones object detection framework [6]. This framework includes new image representation and several levels of classifiers that recognize different sections of a face. Within the Viola-Jones framework, the new image representation is used for quick feature evaluation. The evaluation sets up arbitrary locations of each pixel within the image that was captured [6]. From this data, the software can rearrange and construct a person’s face however it deems suitable. Next, classifiers are used to set up boundaries by searching for important features that will be used in the next step to identify a person’s face.
Face Identification
The final step is the face recognition stage, during which the computer is able to match an identity to an individual’s face by using nodal recognition and principal component analysis. Some algorithms check for up to 80 nodal points, including features such as distance between eyes, nose width, depth of eye sockets, cheekbone placement, and lip thickness. Once nodal points are established, a mathematical algorithm known as principal component analysis is used to compress the dimensions taken by measuring the distance between nodal points [8]. During this step, the program also gets rid of information that is not useful for determining identity. This allows the software to run more efficiently since it will no longer have to search through useless data to find the information it needs.
 Figure 3: Picture of how eigenfaces are used to construct three-dimensional renders of an individual’s face [5].
Figure 3: Picture of how eigenfaces are used to construct three-dimensional renders of an individual’s face [5].
Next, the reduced dimensions are placed into an array. Each array, called an eigenface, contains a collection of differences between the face being analyzed and the average dimensions of the faces in the database [5]. The collection of dimensions within an eigenface can be used to model a person’s face in three dimensions. This allows for the code to get a better idea of what an individual’s face actually looks like, preventing security systems using facial recognition technology from being fooled by just a photograph of a person rather than their actual face. Along with viewing a face in three dimensions, the software may also contain requirements such as having the user blink while their face is being analyzed in order to prevent someone from attempting to fool the system with a photograph [5].
The dimensions are then analyzed for similarities to other faces within the system’s database. The algorithm will either be able to determine if there is a match or if the analyzed face is new to the system based on the magnitude of similarities found between the faces being compared. If a match is made, the code will notify the user that their identity has been confirmed.
Neural Network
Faces that have not yet been encountered by a system’s facial recognition software will be added to its database for future use. The neural network within the software recognizes the dimensions associated with the new face. A neural network is a computer system based off of the human brain and nervous system, which allows for the algorithm to adapt to new faces. A neural network is designed similarly to a human brain; it recognizes patterns and makes logical connections, thus allowing for facial recognition software to achieve more accurate results. This improves the performance of the algorithm, as the faster a system is able to make connections based on past experiences, the quicker an algorithm is able to recognize changes to an individual’s face, such as aging, and learn new faces.
Face Recognition in Security
With continued advancement, facial recognition can be a viable alternative to other forms of authentication such as passwords and fingerprint scanning. Currently, facial recognition is getting its fair share of the security workload. For example, the rise in popularity of online banking within the past few years has created a demand for banks and big business like Wells Fargo and USAA to go the extra mile to protect their clients’ identity from theft. One way banks have worked to accomplish this has been through the use of facial recognition to authenticate activity on an account. Customers open the app of their preferred bank on their smartphone and scan their face with the front facing camera in order to wire money and make withdrawals [4].
Another current example of facial recognition technology being used for security is in airports. Most recently, the Transportation Security Administration (TSA) integrated face recognition technology within the Washington Dulles International Airport. At TSA checkpoints, a computer would scan an individual’s passport as well as their face in order to check for similarities. Law enforcement is thus able to more accurately determine if someone is committing fraud with a stolen passport to travel abroad.
Facial recognition can also be used in large crowd settings. An example of this occurred during the 2001 Super Bowl. Law enforcement strategically placed cameras throughout the Raymond James Stadium in Tampa, Florida, in order to search for and identify anyone who had previously been determined by the FBI as a threat to the safety of those attending the game.
Facial recognition provides a solid platform to move the technology further in the future. To continue the progression of the technology, researchers must solve the challenges of recognizing faces in environments that are not ideal, such as places that have low light or when faces are partially obstructed. With further improvement, facial recognition has the ability to be commercialized outside of law enforcement use to protect an individual’s personal data.
Conclusion
With the increase in usage of facial recognition, the technology behind it will unquestioningly evolve. As the potential of facial recognition is realized, this technology will be increasingly implemented in everyday environments, including those outside of security purposes. Perhaps one day facial recognition will no longer be novel, but rather become a standard way of identification in and out of the world of law enforcement.
References
[1] Dan Tynan (2005, May 18). Biometrics: From Reel to Real [Online]. Available: http://www.pcworld.com/article/120889/article.html
[2] Gary Sims. (2013, September 23). Why fingerprints Shouldn’t be used for Security [Online]. Available: http://www.androidauthority.com/fingerprints-and-security-272092/
[3] Jose Pagiliery (2014, September 16). FBI Launches a Face Recognition System [Online]. Available: http://money.cnn.com/2014/09/16/technology/security/fbi-facial-recognition
[4] Kim Nash. (2016, April 26). Wells Fargo to Verify Customers Through Eye Prints [Online]. Available: http://blogs.wsj.com/cio/2016/04/26/wells-fargo-to-verify-customers-through-eye-prints/
[5] Mathew A. Turk. Face Recognition Using Eigenfaces [Online]. Available: http://cvrr.ucsd.edu/ece172a/fa10/projects/papers/eigenfaces_cvpr.pdf
[6] Paul Viola, Michael Jones. (2003, July 11). Robust Real-Time Face Detection [Online]. Available: http://www.vision.caltech.edu/html-files/EE148-2005-Spring/pprs/viola04ijcv.pdf
[7] Paul Viola, Michael Jones. (2001). Rapid Object Detection Using a Boosted Cascade of Simple Features [Online]. Available: https://www.cs.cmu.edu/~efros/courses/LBMV07/Papers/viola-cvpr-01.pdf
[8] Shang-Hung Lin (2000). An Introduction to Face Recognition Technology [Online]. Available: https://pdfs.semanticscholar.org/490b/775569be1c7d650424fd051f658e288139ba.pdf
[9] Unknown. BBC News. Biometric Technology [Online]. Available: http://news.bbc.co.uk/2/shared/spl/hi/guides/456900/456993/html/
[10] Unknown. Bureau of Justice Statistics. (2015, September) Victims of Identity Theft, 2014 [Online]. Available: http://www.bjs.gov/content/pub/pdf/vit14_sum.pdf