Introduction
Confidentiality: Crisis of Traditional Encryption
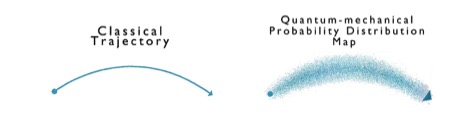
What is a small object? Different people may give different answers based on their personal experiences – a pen is small, a needle is smaller, and the dust is even smaller! However, when zooming into the quantum world, scientists find a place on a much smaller scale than anything that can be seen by human eyes – a place that is dominated by atoms. Comparing to normal world, atoms are unimaginably small, and the normal physical rules in the microscope world will behave in a totally different way in the quantum level [3]. Considering the example of classic projectile motion, people know that particles move in a trajectory that obeys Newton’s laws of motion. In order to observe the motion of a particle, we see the reflection of the light to locate the position of the particle and then draw a relationship between time and position. However, it is very hard to observe particles in the quantum world since electrons possess both particle and wave properties, and the collision of an electron with a photon will actually change an electron’s motion; in other words, we cannot simultaneously know the position and velocity of an electron, which means we cannot obtain the exact trajectory of an electron [3]. Therefore, in quantum mechanics, traditional trajectories are replaced with probability distribution maps, as shown in Fig. 1 [3].
It is a fact that an atom is composed by the neutrons and protons within a nucleus and electrons that orbit around that nucleus. Since atoms are always in motion, scientists use quantum numbers to specify the orientation of the orbital – the spinning motion of the particle [3]. Although quantum numbers could be found arbitrarily, the relationship between each quantum number will always follow the rules of quantum mechanics. After years of studying on quantum mechanics, scientists were able to use the uncertainty of quantum particles to make quantum cryptography – an encryption method that is free of mathematical algorithms; that is to say, quantum cryptography is invincible to hacking, not even quantum computers could decrypt quantum cryptography.
Quantum Cryptography
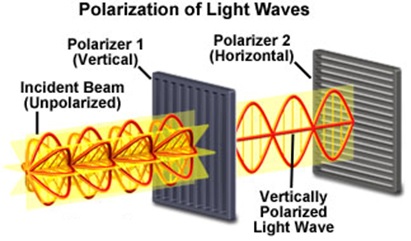
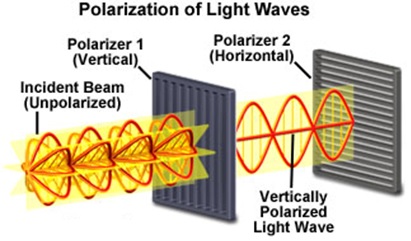
Here is an example of how quantum cryptography works: the sender, Alice, and the receiver, Bob, will establish a secured connection using quantum cryptography. First, Alice will transfer data by sending a series of optical pulses through a fiber wire with each pulse containing a single photon with a specific polarization mode; however, the polarization state of each photon is chosen randomly by Alice, which means no mathematical algorithms are involved in this process. Additionally, Alice will also randomly select half of the sending photons and twist them 45 degrees clockwise before sending them to Bob. Bob then will randomly twist half of the photons he receives 45 degrees clockwise before evaluating their polarization states. Then, Bob and Alice will tell each other which photons they have twisted and compare their photons’ polarization results [4]. Finally, Bob and Alice will discard those results that do not match and keep the polarization represented bits that match exactly the same. Thus, Alice and Bob have created a unique secret key that cannot be hacked since the secret key does not depend on logical algorithms. However, what if there is another person, Eve, who tries to spy on the data they are transmitting? In order for Eve to hack their information, she has to measure the polarization of the photons sent by Alice, but based on the laws of quantum mechanics, attempting to measure the polarization state of a photon will alter its polarization state [5]. As a result, Alice and Bob will notice that the photons received have different polarization states than the photons has been sent, which exposes the fact that Eve has been spying on this connection [4]. Therefore, by using quantum cryptography, people can establish a secured connection that is immune to being hacked.
Although quantum cryptography is ideally invincible, there are still some limitations in building the quantum cryptography system using existing technology. In reality, there is no device can reliably produce only one photon per pulse; instead, some of the pulses will contain two photons while others contain no photons. If two photons were produced in a single pulse, the hacker would simply measure only one of those two photons while leaving the other undisturbed; as a result, the sender and receiver would not notice the presence of the hacker [4]. Fortunately, experiments have demonstrated that a low frequency pulse, such as 10 Hz, will reduce the probability of getting two photons in a single pulse, which eliminate the chance for a hacker to spy on the connection [4]. However, in communication, people expect higher frequency of pulses to transfer large amount of data in a short time; in addition, a reasonable price for quantum cryptography systems is critical for it to be successful in the market. Therefore, scientists must continue perfecting quantum cryptography both technically and financially.
Conclusion
References
-
- [1] Rich, Steven, and Barton Gellman. “NSA Seeks to Build Quantum Computer That Could Crack Most Types of Encryption.” WashingtonPost.com. The Washington Post, 03 Jan. 2014. Web. 23 Feb. 2014.
- [2] Hall, Chris. “China Takes on U.S. in Quest to Be First to Create a Quantum Computer.”Yahoo News UK. Yahoo News, 10 Jan. 2014. Web. 25 Feb. 2014.
- [3] Tro, Nivaldo J. “The Quantum-Mechanical Model of the Atom.” Chemistry: A Molecular Approach. Second Edition ed. New Jersey: Pearson Education, 2011. 277-309. Print. Mt. San Antonio College Edition.
- [4] Benjamin, Simon. “Single Photons “on Demand”” Science 290.5500 (2000): 2273-2274.AAAS. Web. 28 Feb. 2014.
- [5] Dettmer, R., “Light holds the key [quantum cryptography],” IEE Review , vol.51, no.7, pp.32,36, July 2005