Abstract
The Internet has ushered in a new age, marked by the transformation of many sectors of society. Commerce, education, and entertainment have grown to rely on digital applications which increase productivity, provide information forums, and facilitate cultural trends. Often hidden to users, these online applications transform data between layers, enabling digital communication. As the result of decades of innovation, the unique design decisions behind these layers allows data transmission to be high-speed, error resilient, and global.
Introduction
Data transmission is ubiquitous in modern life: transactions are posted to bank balances from storefronts, emails are sent from a sender to a receiver’s inbox, and videos stream from platforms to viewers. With today’s interconnectivity of services, it is hard to imagine that early computers were unable to communicate with each other. Yet, this was the state of computers which the Internet’s earliest pioneers dealt with.
In the pre-Internet age, computers were primarily used by researchers at universities. While computers allowed researchers to perform computations and write documents, they were unable to share their work quickly without a network. Transferring files took an enormous amount of time: a task like sharing a collection of photographs could take over a month [1]. This inefficiency led researchers to develop some of the world’s first computer networks.
ARPAnet, named after the Advanced Research Projects Agency (ARPA) which funded its creation, was one of the first computer networks. It is widely considered the precursor to the modern internet. During the 70s and 80s, ARPAnet connected several universities throughout the United States, including MIT and Stanford. The system allowed researchers to share computing power and information [1]. The ARPAnet experiment rewarded researchers with the lessons of configuring such a network, and many of these lessons were applied to the modern Internet.
Today, the internet is a sprawling interconnection of computer networks spanning the globe. With around 870,000 miles of underwater cabling connecting each of the continents [2], the internet has grown tremendously. To understand what enables the Internet, one must understand its layers of communication.
Abstraction and the Layers of the Internet
The construction of the internet is similar to the automobile design process.
From the theory behind the combustible engine to the components which make up a drive train, there are many processes behind the operation of a car. Is it necessary to know how each distinct component in a car works in order to drive? I certainly don’t think so—yet I still with a general understanding of the brake, accelerator, and steering wheel work. Most drivers employ a concept called “abstraction,” which is defined as viewing something in terms of a generalization without consideration of specific details [3]. Drivers abstract away the knowledge of how a car works. Instead, they concern themselves with knowing how to drive a car, using the features that the car manufacturers expose.
The internet works in a similar way by abstracting the responsibilities of communication into distinct layers. This model allows each successive layer of the internet to focus on its individual role without knowledge of how the other layers work. One such framework that delineates the layers of the internet is the TCP/IP model which has four layers: application, transport, internet, and network access [4].
The Application Layer
Communication between computers is necessary in today’s application landscape. Common tasks like browsing the web, sending an email, or watching a video all rely on internet infrastructure to send and receive data. Data can be any application-specific information necessary to run an app. For a website, its data may include the actual content intended for the user, such as the text or user-interface. Data can also include information which is required to make the service run, such as the login credentials which help an application identify who is making a request.
In order to communicate data over the internet, applications must share a common language. As an analogy, consider typical oral communication. Regardless of where two people grew up in the world, if they share a common language, they can share their ideas, thoughts, and exchange information. In the same way, applications need a “common language” to speak and understand each other. These languages that computers “speak” are called protocols, and they standardize how computers should interact and format data [5]. By adopting these protocols, computers built by different manufacturers share a common means to exchange information.
Hypertext Transfer Protocol
One protocol that is used extensively for browsing the web is the Hypertext Transfer Protocol, more familiarly known as HTTP. It is the protocol that is responsible for mediating how browsers interact with websites. HTTP operates on a client-server model which helps frame the relationship between parties [6]. Clients are users who send HTTP requests to a server who processes the response and sends a corresponding HTTP response [6].
HTTP requests have several components. One important component is the HTTP method [7]. HTTP methods define what action the client is requesting from the server. Some HTTP methods include a GET and POST method. A GET method indicates that the user wants to retrieve information from the server located at the particular URL. The POST method indicates the user is attempting to send information (with the data being sent in the body field) [5].

Figure 1: Example of HTTP Request (left) and HTTP Response (right) [7]
HTTP requests offer many fields which developers can use to make different requests. Some of these fields include the protocol version, status codes, or fields where the developers can add data [7]. Through HTTP, developers have a convention to communicate between servers and clients.
HTTP is just one example of an application layer protocol used to transmit data over the internet, particularly for websites. Other examples of application layer protocols included Simple Mail Transfer Protocol (SMTP) which enables emails to be sent over the internet [8] or the file transfer protocol which defines how files are to be sent from one location on the internet to another [9].
The Transport Layer
The transport layer is responsible for data integrity, ensuring that data is directed towards the correct application and received in the intended order. The transport layer uses subdivision to maintain data integrity. Large chunks of data are split up into many parts called packets [5].
To understand why packets need to be segmented, consider home building. When a contractor builds a home, it is not delivered in one piece from a factory. Rather, materials are brought onto a job site. One reason for this is physical limitation; it can be logistically impractical to transport an entire home because of things like road size or bridge clearance. Similarly, each node in a network can set a constraint on the maximum size of a packet because devices contain limited memory [10]. Thus, in order to meet the maximum transmission unit, packets are divided.
Besides physical constraints, reducing packet sizes can reduce the number of corrupted packets [11]. If each bit of a packet has a 1% likelihood of error, it is expected that at least one bit has an error when transmitting 100-bit packets. On the other hand, if one transmits 10-bit packets, the expected error goes down to 0.1 packets. With smaller amounts of data in each transmission, it is less likely that any single packet is corrupted.
Transmission Control Protocol
One important protocol that is used in the transport layer is the Transmission Control Protocol (TCP) [12]. TCP segments application data from the previous layer into packets and adds on information regarding the source port, the destination port and the sequence number [13]. Ports are similar to the departure gate at an airport. The gate number specifies which flight you are going on to arrive at a specific destination. In the same way, computer applications declare port numbers on which they are listening for specific types of communication. In this way, packets can be sent to the right location on a different device. The packet also includes the sequence number in order to ensure that data arrives in the correct order. Constructing packets in this fashion allows TCP to be a robust protocol enabling data to be transmitted across networks in order and be resistant to errors resulting from large packet sizes.
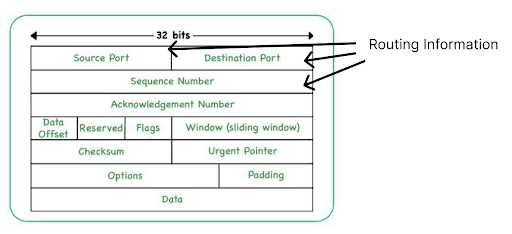
Figure 2: Example of a TCP Packet Adapted from [13]
Communication channels are often noisy, meaning that data can become corrupted in the process of transportation. [14]. Protocol designers were aware of this limitation and constructed around it. Rather than create error-free mediums of transportation, protocols included methods to detect and resolve errors. This allowed protocols to be resilient despite unpredictable transportation errors. Under the transmission control protocol, if an error is detected, the sender retries sending the packet until it is successful. TCP utilizes parity checks, among other methods, to detect errors. Parity checks detect “bit flip” errors which occur when the intended sequence of bits differs from the sequence that was received. For example, a sender may transmit ‘101’, but the receiver gets ‘111’. In this case, the second ‘0’ flips to a ‘1’. An example of a bit flip error is shown below in Figure 3.

Figure 3: Bit Flip Error (not using parity bit)
In order to resolve bit flip errors, TCP utilizes a special bit called the parity bit. A parity bit is the last bit sent in a sequence, and it is used to make the total count of ones even. [14]. For example, if the initial sequence was ‘100’, the parity bit would make the sequence ‘1001’ so there is an even number of 1’s. If there was an odd number of bit flips, the parity bit would mismatch the sequence, indicating an error. If the packet has an error, TCP requires that the receiver notify the sender to resend the original packet. In this way, the application layer can depend on the data received.
The Internet Layer
Whereas the previous layers of the internet were concerned about ensuring that the content of data is communicable and that the data is packaged appropriately for transmission, the internet layer directs packets through the network to reach their appropriate destinations [13]. In other words, the internet layer is the “navigator” of the internet.
This layer is similar to how packages move between different nodes within the Amazon distribution network. When you buy a product from Amazon, your package may go from the seller to a regional distribution hub. There may be several other facilities your package goes through before being sent to your home. The internet layer is responsible for knowing which “distribution” center to send your data to so it can arrive at your computer. In our analogy, the different nodes of the network are not distribution centers but devices called routers [15].
In the same fashion as the other layers, there is also a protocol to standardize this process called the internet protocol or IP [15].
Internet Protocol
The internet protocol attaches information to the packets constructed in the previous transport layer in order to direct packets to their next hop. The internet protocol uniquely identifies networks by IP addresses which are sequences of numbers which take the form NNN.NNN.NNN.NNN [16]. An example of an IP address following this scheme is 192.168.0.1. The internet protocol appends the destination IP address to the current packet, allowing intermediary routers to use their knowledge of the network to best guide the packet to its final destination.
Routers use structures called “routing tables” to store network information [17]. These tables are used to determine the next stop, which is often an intermediary router. One popular algorithm to create routing tables is called distance vector routing. Under a distance vector routing algorithm, nearby routers notify each other of their estimates for the best paths to different destinations; eventually, as information is communicated, each router is able to determine the true best path [18]. This allows routers to send data without complete knowledge of the network. An example of a routing table is shown below in Figure 4.
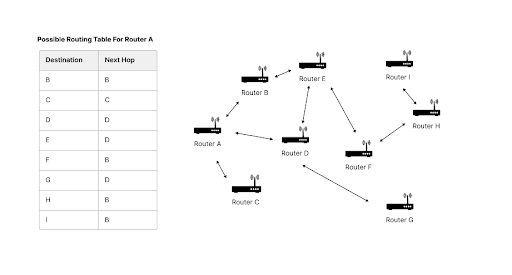
Figure 4: Sample Routing Table
Using a routing table, an intermediary router would update the packet it received with the IP address of the next router on the path to the destination. Finally, once the packet is transported to the correct local area network, a MAC address (which is a device specific address, most often to your computer’s network adapter) will be used to send the packet to the correct computer [17].
The Network Access Layer
The network access layer is responsible for the conversion of binary packets to physical signals. These signals may be electric, radio, or an optical signal depending on the implementation used by the network operator.
Different Mediums of Transmitting Information
One familiar implementation of the network access layer is WiFi. WiFi utilizes radio waves to transmit information [19]. Special computer chips called wireless adapters translate binary information into radio waves. These waves are captured by wireless routers using antennas. Because WiFi is considered impractical for long range communication, wireless routers pass the information along a wired connection to the rest of the internet [19]. This process is standardized in a family of protocols called 802.11 which define the expectations of devices which communicate over WiFi [19].
Ethernet is an alternative implementation of the network access layer. It is a wired connection between routers. 1000BaseT is one standardization of ethernet which uses fiber optic cables [20]. Fiber optic cables transmit data over light using laser pulses [21], and speeds can depend on physical features of the cable including the core size (the light guiding portion) [22]. The technology has advanced so far that the state of the art can transmit data at 1.84 petabits per second which is equivalent to streaming 122 million netflix movies at the same time [21]. Because of its high speed capability and long range, ethernet is the primary technology which transmits digital information.
Conclusion
If the history of the internet offers any lesson about its future, it’s that the internet progresses dramatically and unpredictably. It was originally used as a tool by a small set of researchers to share information. Today, it is the bedrock of modern society, connecting the lives of billions of people. The design decisions which separated the internet into distinct layers have allowed technologies to scale at unprecedented levels enabling global products and services. These backbones of the internet are unlikely to shift, yet they will cause tremendous change in the future. It is upon these layers which new services will erupt using the same principles of abstraction and standardization. Whether it is the rise of AI personalized search engines or immersive virtual reality experiences, the layers of the internet will be instrumental in powering the technology of tomorrow.
Links for Further Reading:
- Laser LiFi Could Send Data Speeds Soaring: https://spectrum.ieee.org/laser-lifi-could-send-data-speeds-soaring
- The global internet is powered by vast undersea cables. But they’re vulnerable: https://www.cnn.com/2019/07/25/asia/internet-undersea-cables-intl-hnk/index.html
- New Fiber Optics Tech Smashes Data Rate Record: https://spectrum.ieee.org/fiber-optic-cable-record
Links to Watch More:
- How the Internet Travels Across Oceans: https://www.youtube.com/watch?v=yd1JhZzoS6A
- The first Internet connection, with UCLA’s Leonard Kleinrock: https://www.youtube.com/watch?v=vuiBTJZfeo8
- Reliable data transmission: https://www.youtube.com/watch?v=eq5YpKHXJDM
References
[1] M. Bay, “Conversation with a pioneer: Larry Roberts on how he led the design and construction of the ARPANET,” Internet Histories, pp. 69-73, 2019. Accessed: Sept. 19, 2024, doi: 10.1080/24701475.2018.1544727. [Online.] Available: https://www-tandfonline-com.libproxy2.usc.edu/share/II8RQGBHDKB5ZP6RMRM8?target=10.1080/24701475.2018.1544727
[2] H. Guinness. “The world’s internet traffic flows beneath the oceans—here’s how.” popsci.com. Accessed: Sep. 5, 2024. [Online.] Available: https://www.popsci.com/technology/google-nuvem-cable/.
[3] M. Ward, “A definition of abstraction,” Journal of Software Maintenance: Research & Practice, vol. 7, no. 6, p. 443, Nov./Dec. 1995. Accessed: Sept. 19, 2024, doi: 10.1002/smr.4360070606. [Online.] Available: https://libproxy.usc.edu/login?url=https://search.ebscohost.com/login.aspx?direct=true&db=aci&AN=13260985&site=ehost-live&scope=site
[4] P. B. Nath, and M. M. Uddin, “TCP-IP Model in Data Communication and Networking,” AJER, vol. 4, no. 10. Accessed: Sept. 19, 2024. [Online.] Available: https://www.ajer.org/papers/v4(10)/N04101020107.pdf
[5] “How does the Internet work?” cloudflare.com. Accessed: Sept. 5, 2024. [Online.] Available: https://www.cloudflare.com/learning/network-layer/how-does-the-internet-work/.
[6] “What is HTTP?” pubnub.com. Accessed: Sept. 11, 2024. [Online.] Available: https://www.pubnub.com/guides/http/
[7] “An overview of HTTP.” mozilla.org. Accessed: Sept. 11, 2024. [Online.] Available: https://developer.mozilla.org/en-US/docs/Web/HTTP/Overview
[8] D. Lepilkina, “Understanding SMTP – The Protocol Behind Email Delivery.” Accessed: Sept. 11, 2024. [Online.] Available: https://mailtrap.io/blog/smtp/#SMTP-commands-and-responses
[9] C. Mitchell, “File Transfer Protocol (FTP) Meaning and Uses.” investopedia.com. Accessed: Sept. 11, 2024. [Online.] Available: https://www.investopedia.com/terms/f/ftp-file-transfer-protocol.asp
[10] “What is MTU (maximum transmission unit)?” cloudflare.com. Accessed: Sept. 11, 2024. [Online.] Available: https://www.cloudflare.com/learning/network-layer/what-is-mtu/
[11] S. Roy, “Maximum Packet Size for a TCP Connection.” baeldung.com. Accessed: Sept. 11, 2024. [Online.] Available: https://www.baeldung.com/cs/tcp-max-packet-size
[12] “What is TCP (Transmission Control Protocol)?” geeksforgeeks.org. Accessed: Sept. 11, 2024. [Online.] Available: https://www.geeksforgeeks.org/what-is-transmission-control-protocol-tcp/
[13] “TCP/IP Packet Format.” geeksforgeeks.org. Accessed: Sept. 11, 2024. [Online.] Available: https://www.geeksforgeeks.org/tcp-ip-packet-format/
[14] D. Goodwin. “Methods and Algorithms in Error Checking for Serial Communications.” control.com. Accessed: Sept. 5, 2024. [Online.] Available: https://control.com/technical-articles/methods-and-algorithms-in-error-checking-for-serial-communications/.
[15] “What is a router?” cloudflare.com. Accessed: Sept. 11, 2024. [Online.] Available: https://www.cloudflare.com/learning/network-layer/what-is-a-router/
[16] C. F. Bowman, “How Does the Internet Work?,” in How Things Work, 1st ed., vol. 1, United Kingdom: CRC Press, 2023, pp. 121–142. doi: 10.1201/9781003143437-7. [Online.] Available: https://www-taylorfrancis-com.libproxy1.usc.edu/reader/download/94531624-5325-4804-8e4b-1b0a7f2cba87/chapter/pdf?context=ubx
[17] “What is the Internet Protocol?” cloudflare.com. Accessed: Sept. 11, 2024. [Online.] Available: https://www.cloudflare.com/learning/network-layer/internet-protocol/
[18] “What is routing?” amazon.com. Accessed: Sept. 19, 2024. [Online.] Available: https://aws.amazon.com/what-is/routing/
[19] M. Brain and T. Homer. “What is WiFi and How Does it Work?” computer.howstuffworks.com. Accessed: Sept. 5, 2024. [Online.] Available: https://computer.howstuffworks.com/wireless-network.htm.
[20] “Ethernet Standards and Protocols Explained.” computernetworkingnotes.com. Accessed: Sept. 11, 2024. [Online.] Available: https://www.computernetworkingnotes.com/networking-tutorials/ethernet-standards-and-protocols-explained.html
[21] K. Hulick. “A single chip like this could transmit a world’s worth of data.” snexplores.org, Accessed: Sep. 5, 2024. [Online.] Available: https://www.snexplores.org/article/innovation-2023-computer-chip-data-transmission-record
[22] J. Hecht. “Bringing Legacy Fiber Optic Cables Up to Speed.” IEEE.org. Accessed: Sept. 5, 2024. [Online.] Available: https://spectrum.ieee.org/legacy-fiber-optic-cables-speed-data-rates.


