Abstract
Have you ever forgotten your password on a website where you made an account months before? The process of retrieving that password begins with a trial and error process of running through your familiar passwords and usually ends with a frustrated click on the “Forgot password?” button nearby. After refreshing your inbox in search of an email the website sent you, the instructions on how to access your account finally arrive. Here’s the red flag: that email contains your old password in plain text. If you find yourself in this position, you are forced to question the security of that website and consider erasing your account.
Introduction
Internet security is becoming an increasingly important concern in this digital age, especially as we find ourselves storing an exponential amount of personal and private information online. Here’s a helpful hint: never store your passwords in plain text. Doing so increases the potential risk of security breaches to online databases and, perhaps more importantly, your own account information. If a hacker were to break into a password database filled with plain-text passwords, they would have immediate access to a number of accounts. This is where the importance of cryptography, or more specifically, encryption, comes into play for the creation of secure data systems.
Cryptography is the science of communicating information securely from one source to another. You may not notice the daily usage of cryptography in your own life, but its importance cannot be understated. Today, cryptography is widely used throughout communication and payment systems such as e-commerce websites, cell-phones, credit cards, and computer passwords. The goal of using cryptography is to prevent third parties from gaining access to personal data. Today, sensitive information such as bank account details or social security numbers can be entered online thanks to cryptography and its ability to create a secure means of transmitting data. As hacking techniques and identity theft become more sophisticated, cryptography will become one of the most important security measures in protecting personal data.
Principles of Cryptography
Cryptography has three main goals for providing security. First among these is data integrity. When sending messages between two sources, the recipient of the message should be capable of distinguishing whether or not the message was tampered with. In other words, the recipient should be able to discern whether or not a particular part of the message has been falsified. The second goal in maintaining secure communications is authentication. When a message is received, the recipient should be able to verify who the sender is. Finally, cryptography also aims to solidify non-repudiation – meaning that after a message is delivered, the sender should not be capable of refuting that they were the original author [4]. Successful cryptography must accomplish all of these goals: integrity, authentication, and nonrepudiation. For messages written with pen on paper, it is relatively easy to accomplish these goals as personal signatures provide a means for verifying the original author and his or her intent. However, as we continue our advancement into a digital era of communication, meeting the goals of cryptography becomes much more difficult.
History of Cryptography
The practice of cryptography has been around for centuries, and examples of encrypting messages have been dated all the way back to 1900 B.C.E in Egypt. The Atbash cipher was used to encrypt Hebrew messages by replacing the first letter of the Hebrew alphabet with the last letter, the second letter with the second to last, and so on until the alphabet is effectively reversed [1]. A cipher is the set of instructions for encrypting a message, and a “key” is the clue on how to effectively decrypt and read the message. One of the most famous examples of cryptography was what is known as Caesar’s cipher. Julius Caesar would encrypt his messages to his generals by using a substitution cipher in which each letter of the alphabet is shifted a certain number of positions. In this case, Caesar shifted each letter by 3 so that he could securely send messages to his officers, whom he entrusted with the key to deciphering these messages. The word “cryptography,” for example, would instead be written as “fubswrjudskb” as described in Figure 1.
Figure 1: Demonstrates a substitution cipher with a shift of 3. Each arrow points to the corresponding letter in the shifted alphabet [3].
With the advent of computers and the digital era, basic ciphers and encryption methods are no longer the most successful means of securing information. Computers allow for brute force solution methods which make ciphers, such as Caesar’s cipher, quite brittle. During the 1970’s, the United States government deemed it necessary to create a standard for encrypting sensitive information. A team of researchers at IBM came up with a solution to the government’s needs by creating an algorithm for encrypting data using symmetric-key cryptography.
Symmetric-Key Cryptography
Symmetric-key cryptography is a fundamental form of cryptography that involves exchanging a message between two parties. First, the two parties agree on a key to use when encrypting and decrypting messages. Before sending a message to party B, party A encrypts that message using an encryption algorithm and the key agreed upon by both parties. After party B receives the encrypted message, they use the key to decrypt the ciphertext back into plain-text. This type of cryptography is called symmetric-key cryptography because both communication parties use the same key for encryption and decryption [4].
Figure 2: Illustration demonstrating each step of the process in symmetric key encryption [5].
Symmetric-key encryption provides a very fast and efficient way for encrypting messages, but does pose a number of security flaws. The key for unlocking the message must be shared with both parties in secure fashion before the message is sent. If an attacker were to gain access to the key, they would easily be able to decipher each party’s messages. Due to its speed, symmetric-key encryption is useful for encrypting large amounts of data. The problem that symmetric key encryption faces is how to share the key in a secure way. This flaw is what led to the creation of public-key cryptography 40 years later.
Public-Key Cryptography
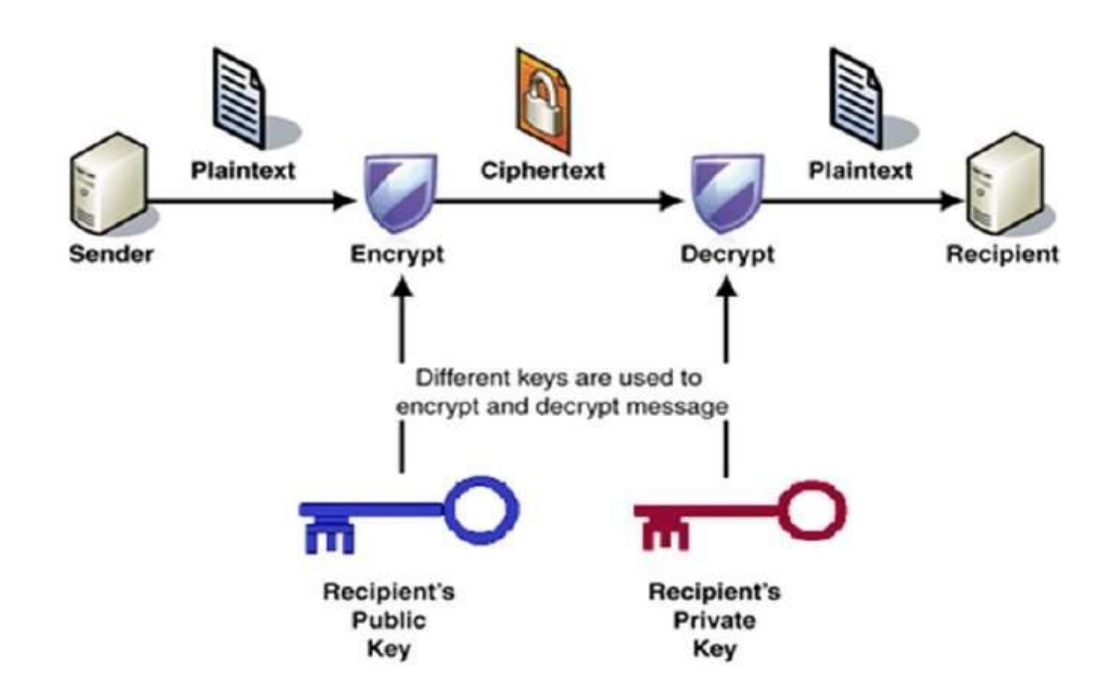
Unlike with symmetric-key cryptography, like its name suggests, public-key cryptography uses a public key for encrypting data. In a public-key encryption system, each communicating party has a pair of keys. The public key, used for encrypting messages, can be distributed to anyone, while the user’s private key must be kept a secret. In this system, if party A wanted to send a secure message to party B, party A would first encrypt their message using party B’s public key. The only way to decrypt a message which uses party B’s public key is by using B’s private key [2].
Figure 3: Step by step process of public-key encryption demonstrating the use of different keys during the encryption/decryption phases. [6]
An example of public-key cryptography is its use in Transport Layer Security (TLS). TLS provides privacy and data integrity between a client (e.g. your web browser) and a server (e.g. amazon.com). When connected to the internet using TLS, data is encrypted using symmetric-key cryptography before being sent. The client and server agree on which key to use before any data is transmitted. The identity of the two communicating parties is then authenticated using public-key cryptography [7]. You can see when TLS is being used by looking at the address bar in your web browser. If you see the web address starts with “https,” you know your information is most likely secure.
Encryption methods such as symmetric or public key cryptography are designed to be provably secure. That is to say, the cryptographic algorithm can be mathematically proven to resist certain types of attacks. The security of an algorithm is usually based off a number of assumptions about the attacker’s ability. It is assumed that the attacker does not possess unlimited computational power, and that certain underlying assumptions in mathematics remain to be true. One of the most widely used public-key cryptographic algorithms, RSA, is based off of the idea that computing the prime factors of large integers is infeasible. Therefore, when calculating the security of RSA, it is presumed that the attacker is incapable of doing such a task.
Future of Cryptography and Encryption
Cryptography is constantly trying to stay ahead of attackers in order to provide a secure way of transferring data. As computers become more powerful, cryptographic algorithms must be complex enough to make brute force decryption attempts unfeasible. Quantum cryptography has been suggested as a solution to the security risk of sharing the key in symmetric-key cryptography. Quantum mechanics can be used to generate a key to encrypt data, just like with normal computing. But unlike with typical encryption keys, measuring a quantum system disturbs the system. If an attacker tries to read the key while it is being generated the system will abort its communication attempts [8]. This theoretically provides unconditional security in communication, as symmetric keys can be shared without fear of being intercepted by a hacker. Quantum computers and quantum cryptography are still in research development; it will take many years before quantum technology sees widespread use. As quantum computers move closer to becoming a technological reality, the future of cryptography is headed towards creating systems that are resistant to attacks by quantum computers.
Conclusion
It is easy to overlook cryptography’s impact on keeping our information secure. Not too long ago, in the “dark ages,” consumers were unable to purchase goods online or check their bank statements from their home computer. With the introduction of more advanced cryptography and security protocols such as HTTP, the World Wide Web has become a much safer place for providing sensitive information. It may be some time before cryptography provides unconditional security; however, the field of cryptography has made great strides in creating secure communication methods over the last several decades. E-commerce websites, cell-phones, credit cards, and password security innovation have flourished with cryptography. Only time will tell what new inventions cryptography will give rise to.
References
[1] B. M. Metzger and M. D. Coogan, The Oxford companion to the bible. Oxford [etc.]: Oxford University Press, 2004.
[2] S. Vaudenay, A classical introduction to Cryptography: Applications for communications security. New York: Springer-Verlag New York, 2005
[3] P. Thorsteinson and G. A. G. Ganesh, .NET security and cryptography. United States: Prentice Hall PTR, 2003.
[4] H. Delfs and H. Knebl, Introduction to cryptography: Principles and applications, 3rd ed. 2015.
[5] K. Krishnan, “SFWR 4C03: Computer Networks and Computer Security,” in North Carolina State University, 2004. [Online]. <http://www4.ncsu.edu/~kksivara/sfwr4c03/lectures/lecture9.pdf>.
[6] “Public key Encryption,” www.tutorialspoint.com, 2016. [Online]. Available: http://www.tutorialspoint.com/cryptography/public_key_encryption.htm. Accessed: Sep. 7, 2016.
[7] T. Dierks, “The transport layer security (TLS) protocol version 1.2,” 2008. [Online]. Available: https://tools.ietf.org/html/rfc5246. Accessed: Sep. 8, 2016.
[8] H.-K. Lo, M. Curty, and K. Tamaki, “Secure quantum key distribution,” Nature Photonics, vol. 8, no. 8, pp. 595–604, Jul. 2014.