Origins
How It Works
RFID
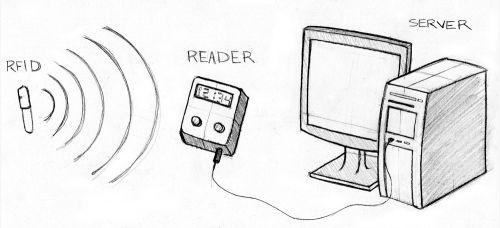
The RFID, or transponder, sends out a unique signal that allows the Reader to identify its location and identification. There are two types of transponders: passive and active. Passive transponders are smaller in size, do not require power, and have long-term operation capacity. Since they do not actively broadcast their signal, they require an external radio wave to establish contact and initiate data request. This is the type of transponder used in healthcare informatics. Active transponders require battery power to broadcast signals to the Reader, but transmissions are more reliable.
Reader
Server
Operations and Breakdown
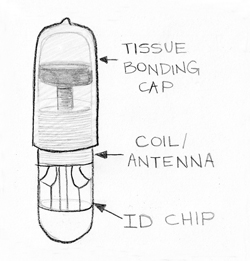
The microchip introduced for healthcare applications is a passive transponder (see Fig. 2). It is 11 millimeters long and about 1 millimeter in diameter, comparable to the size of grain of rice. It consists of a tissue-bonding cap made from a special plastic that covers a sealed glass capsule containing the RFID circuitry. The cap is designed to bond with human tissue and prevent the capsule from moving around once it has been implanted. The coils of the antenna turn the reader’s varying magnetic field into current that powers the chip. The coil is coupled to a capacitor to form a circuit that resonates at 134 KHz (Low Frequency). The chip modulates the amplitude of the current going through the antenna to produce a 128 bit signal, which translates into 16 decimal digits.
Current Uses
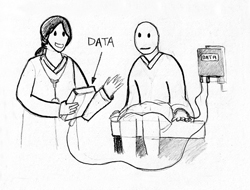
Biomedical engineers have been tailoring microchip technology to fit a wide range of medical applications. Positive ID has a division specifically for the healthcare sector, known as Health ID (see Fig. 3). Beyond patient identification and medical storage microchips, which are presently available for about $150, the company has two other systems: the Glucose-Sensing Microchip and the Rapid Virus Detection System. The Glucose-Sensing Microchip is an implantable device that measures glucose levels in the body in real time. Phase I studies, which involve tests of the signaling components of the technology, have been completed. In ongoing Phase II studies, researchers are working to enhance the glucose response in the presence of blood to provide more accurate readings. A Rapid Virus Detection System is also under development. The proposed non-invasive device would check a patient’s fluids for viruses within minutes, rather than hours. If viruses are present, it instantly breaks it down into main parts in order to identify and treat it [3].
Future Applications
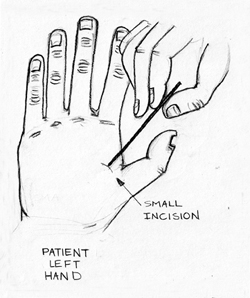
As EMR merges with microchips and worldwide databases, globalized access will allow patients to receive proper care in hospitals at any location. However, some changes will have to take place to ensure the functionality of this relationship. First, medical offices will have to conform to worldwide standards. Second, a central implant location will have to be determined so that medical professionals will know where to look for the microchip (Left Hand Outpatient Procedure Shown in Fig. 4).
Limitations
Use of this technology has ethical and technological limitations. From an ethical perspective, there are growing concerns over issues stemming from the inability to deactivate the device. Confidential information such as location, bank accounts, medical information and blood monitoring data might be easily transferred to anyone with a reader and the right set of passwords, with or without the user’s consent (see Fig. 5). In the healthcare sector, liability regulations would have to be revisited so that unauthorized access to sensitive patient data would not lead to mistrust and lawsuits against hospitals. As use of the microchip spreads to other industries, such as with parents tagging their children to protect against kidnapping, the question of whether children should have a vote in this process also becomes an ethical dilemma [10]. Within that same realm, some believe we will reach a moment in time when choice will turn into a requirement. They predict that the popularity of the microchip will increase at such an exponential rate that government regulations will force the population to implant these devices in order to receive general healthcare benefits [11].
Conclusion
References
-
- [1] S. Granneman. (2003, June).”RFID Chips Are Here.” The Register: Sci/Tech News for the World. [On-line]. Available: http://www.theregister.co.uk/2003/06/27/rfid_chips_are_here/ [Oct. 25, 2003].
- [2] RFID, Journal. (2005, Dec.). “The History of RFID Technology – RFID Journal.” RFID Journal – RFID (Radio Frequency Identification) Technology News & Features. [On-line]. Available: http://www.rfidjournal.com/article/view/1338 [Oct. 25, 2010].
- [3] VeriChip. “HealthID.” Internet: http://www.positiveidcorp.com/health-id.html, Aug. 01, 2004 [Oct. 14, 2010].
- [4] W. Yao et al. “The Use of RFID in Healthcare: Benefits and Barriers,” in Proceedings of 2010 IEEE International Conference on RFID-Technology and Applications (RFID-TA), 2010, pp. 128-34.
- [5] S. Y. Lee et al. (2010, July). “A Low Power RFID Integrated Circuits for Intelligent Healthcare Systems.” IEEE Trans Inf Technol Biomed. [On-line]. Vol. 1.1 PubMed. Available: http://www.ncbi.nlm.nih.gov.libproxy.usc.edu/pubmed/20615816 [Oct. 15, 2010].
- [6] A. Nassim. (2009, Mar.). “What Is a Verichip?” Electrical and Electronics. Electrical and Electronics Portal. [On-line]. 2010. Available: http://electricalandelectronics.org/2008/11/17/what-is-a-verichip/ [Oct. 25, 2010].
- [7] E. Lutton et al. “PATIENT IDENTIFICATION WITHIN A HEALTHCARE SYSTEM: The Role of Radio Frequency Identification and Bar Code Technologies,” in Proceedings of 11th International Conference on Mathematical Methods and Computational Techniques in Electrical Engineering/Applied Computing Conference, 2009, pp. 17-23.
- [8] P. Chen. “Implementation of an RFID-based Management System for Operation Room,” in International Conference on Machine Learning and Cybernetics. Proc. of Proceedings of 2009 International Conference on Machine Learning and Cybernetics., 2009, pp. 2933-2938.
- [9] HIMSS (Healthcare Information and Management Systems Society). (2006, Apr.). “The Legal Electronic Medical Record. Chicago: Healthcare Information and Management Systems Society (HIMSS).” HIMSS (Healthcare Information and Management Systems Society). [On-line]. Available: http://www.himss.org/ASP/index.asp [Oct. 20, 2010].
- [10] B. Chowdhury and C. D’Souza. “Challenges and Opportunities Relating to RFID Implementation in the Healthcare System,” presented at the Business Information Processing LNBIP 20.3rd International United Information Systems Conference, UNISCON, Germany, 2009.
- [11] T. Monahan and J. A. Fisher. (2010, Oct.). “Implanting Inequality: Empirical Evidence of Social and Ethical Risks of Implantable Radio-frequency Identification (RFID) Devices.” Cambridge University Press. [On-line]. Vol. 1.1. Available: http://journals.cambridge.org.libproxy.usc.edu/action/displayAbstract?fromPage=online&aid=7911612&fulltextType=RA&fileId=S0266462310001133 [Oct. 15, 2010].
- [12] Y. Zuo. “Survivable RFID Systems: Issues, Challenges, and Techniques.” Systems, Man, and Cybernetics, Part C: Applications and Reviews, IEEE Transactions. [On-line]. Vol. 40.4, pp. 406-418, 2010.
- [13] A. Bahney. (2006, Feb.). “High Tech, Under the Skin.” The New York Times. [On-line]. Available: http://www.nytimes.com/2006/02/02/fashion/thursdaystyles/02tags.html? sq=rfid&st=cse&scp=14&pagewanted=all [Oct. 15, 2010].
- [14] L. L. Chen et al. “Using RFID to Realize Human Computer Interaction.” IEEE, vol 978-1-4244-5228-6, 2009.
- [15] J. Edwards. (2010, Sept.). “Human or Cow, PositiveID Has an Implantable Microchip for You | BNET.” BNET. The CBS Interactive Business Network. [On-line]. Available: http://www.bnet.com/blog/drug-business/human-or-cow-positiveid-has-an-implantable-microchip-for-you/5772 [Oct. 14, 2010].
- [16] S. Gossett. (2004) “Paying for drinks with wave of hand: Club-goers in Spain get implanted chips for ID, payment purposes.” WordNetDaily. [On-line].
- [17] Available: http://www.wordnetdaily.com/news/article.asp?ARTICLE_ID=38038.
- [18] L. Ho et al. “A Prototype on RFID and Sensor Networks for Elder Healthcare: Progress Report,” in Proceedings of the 2005 ACM SIGCOMM Workshop on Experimental Approaches to Wireless Network Design and Analysis Table of Contents, 2005.
- [19] S. Kirsner. (2010, Jan.). “Imbedded Chips Track Drug Doses, Health Shifts.” The Boston Globe. [On-line]. Available: http://www.boston.com/business/technology/articles/2010/01/11/investors_place_165_million_bet_on_microchips_implantable_devices/ [Oct. 15, 2010].
- [20] L. Kohn et al. (2000, Oct.). “To Err Is Human, Building a Safer Health System.” The National Academy Press. Institute of Medicine. [On-line]. Available: http://www.nap.edu/openbook.php?record_id=9728 [Oct. 20, 2010].
- [21] J. Markoff. (2006, Mar.). “Study Says Chips in ID Tags Are Vulnerable to Viruses.” The New York Times. [On-line]. Available: http://www.nytimes.com/2006/03/15/technology/15tag.html?_r=1 [Oct. 14, 2010].
- [22] S. Morrissey. (2007, Oct.). “Are Microchip Tags Safe? – TIME.” Time Magazine. [On-line]. Available: http://www.time.com/time/health/article/0,8599,1672865,00.html [Oct. 14, 2010].
- [23] National Conference of State Legislatures (NCSL). “Privacy Legislation Related to Radio Frequency Identification (RFID).”
- [24] Internet: http://www.ncsl.org/programs/lis/privacy/rfid06.htm, 2006.
- [25] M. I. Songini. (2007) “ND bans forced RFID chipping. Governor wants a balance between technology, privacy, Computerworld.” Computer World. [On-line].
- [26] Available: www.computerworld.com/action/article.do?command=viewArticleBasic&taxonomyId=15&articleId=9016385&intsrc=hm_topic.
- [27] R. Stein. (2004) “ID chip for humans wins approval by FDA.” The Seattle Times. [On-line].
- [28] Available: http://seattletimes.nwsource.com/html/nationworld/2002062686.chip14.html.
- [29] R. Want. (2008, Aug.). “RFID–A Key to Automating Everything: Scientific American.” Scientific American. [On-line]. Available: http://www.scientificamerican.com/article.cfm?id=rfid-key-automats-everything [Oct. 14, 2010].
- [30] R. Waters. (2006) “US Group Implants Electronic Tags in Workers.” Financial Times. [On-line].
- Available: www.ft.com/cms/s/ec414700-9b4-11da-8baa-0000779e2340.html.


